Leyka WordPress Plugin Multiple Vulnerabilities

Researcher
This vulnerability was discovered by @yuyudhn.
Details
Detail about Leyka WordPress Plugin.
| Parameter | Value |
|---|---|
| Software | Leyka |
| Description | Leyka is a plugin for crowdfunding and donations collection via WordPress website. |
| Type | WordPress Plugin |
| Developer | Teplitsa |
| Plugin URL | https://wordpress.org/plugins/ultimate-landing-page |
| Vulnerable Version | < 3.30 |
| Classification | Cross-Site Scripting, Broken Access Control |
| Required privilege | Unauthenticated |
| Publicly disclosed | 03.03.2023 |
CVE-2023-27442
The Leyka plugin for WordPress is vulnerable to Cross-Site Request Forgery in versions up to, and including, 3.29.2. This makes it possible for unauthenticated attackers to perform an unknown action granted they can trick a site administrator into performing an action such as clicking on a link. The impact of this vulnerability is unknown.
Status: Patched at Leyka 3.30.
The developer add nonce to prevent CSRF at Leyka Plugin.

CVE-2023-27450
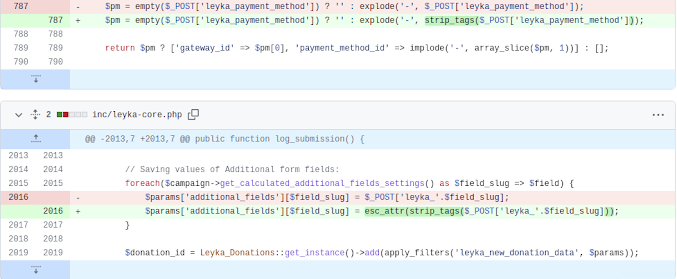
The Leyka plugin for WordPress is vulnerable to Stored Cross-Site Scripting in versions up to, and including, 3.29.2 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Status: Patched at Leyka 3.30.
The developer add esc_attr to prevent XSS at Leyka Plugin.
References
- Github Commit #1
- Github Commit #2
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/leyka/leyka-3292-cross-site-request-forgery
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/leyka/leyka-3292-unauthenticated-stored-cross-site-scripting
